DDoS Attack Disrupts Kaveri 2.0 Portal Operations
Syllabus:
GS-3:
Cyber Security
Focus:
The Kaveri 2.0 portal, responsible for property registrations in Karnataka, was targeted by a DDoS attack in early 2025, disrupting services and registrations. The attack exposed vulnerabilities in government systems, raising concerns about cybersecurity in public sector digital infrastructure.
Understanding the Kaveri 2.0 Incident:
- What Happened to Kaveri 2.0?
- Kaveri 2.0, a web-based portal, is designed to streamline property registrations in Karnataka.
- In January 2025, the portal faced intermittent and severe server outages that hindered its functioning.
- The Revenue Department and E-Governance Department investigated the issue and determined that the outages were not due to technical issues, but instead caused by a Distributed Denial of Service (DDoS) attack.
- The attack significantly affected the portal’s performance, especially in the processing of Encumbrance Certificates (EC) and property registrations.
- Initial Response and Investigation
- Following the disruption, A. Dayananda, the Inspector General of Registrations, lodged a formal complaint with the Cyber-Crime Police.
- The Cybercrime, Economic Offences, and Narcotics (CEN) police filed a case under the Information Technology Act, 2000 against the unidentified perpetrators.
Understanding DDoS Attacks:
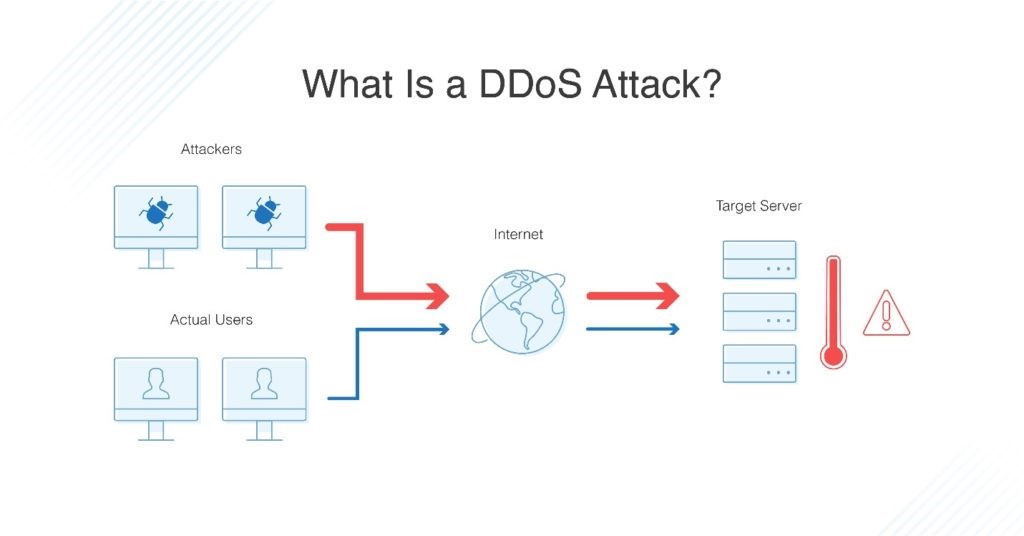
What is a DDoS Attack?
- A Distributed Denial of Service (DDoS) attack involves overwhelming a targeted system (server, network, or service) with massive volumes of internet traffic, rendering the service unavailable.
- Unlike a regular Denial of Service (DoS) attack that originates from a single source, a DDoS attack is orchestrated by using a botnet (a network of compromised systems infected with malware) to flood the target with excessive requests.
Mechanics of a DDoS Attack
- The primary aim is to saturate the bandwidth of the target, exploit vulnerabilities in the network stack, or target specific weaknesses in applications and services.
- DDoS attacks can result in service downtimes, making the targeted service inaccessible to users and causing financial losses due to disrupted operations.
- While DDoS attacks do not directly steal data, they can serve as a distraction for other malicious activities, such as data breaches.
- Such attacks can damage an organization’s reputation, erode customer trust, and raise doubts about the firm’s ability to handle cybersecurity threats.
Differences Between DoS and DDoS Attacks:
- Definition
- DoS (Denial of Service): A cyberattack aimed at disrupting the normal functioning of a system by overwhelming it with excessive traffic from a single source.
- DDoS (Distributed Denial of Service): A similar attack, but it uses multiple compromised systems, making it much harder to stop.
- Source of Attack
- DoS: The attack comes from a single system targeting the victim system.
- DDoS: The attack comes from multiple systems attacking the victim system simultaneously.
- Data Packet Flow
- DoS: The victim’s system is overloaded with data packets from one location.
- DDoS: Data packets are sent from various locations (multiple devices), creating a broader impact.
- Speed of Attack
- DoS: The attack progresses slower due to only one system involved.
- DDoS: DDoS attacks are faster as they leverage multiple systems (botnets).
- Blocking the Attack
- DoS: Easier to block as the attack originates from a single system.
- DDoS: Harder to block due to traffic coming from multiple sources.
- Traceability
- DoS: Easier to trace as it is a single source attack.
- DDoS: Difficult to trace as it comes from many different systems and locations.
- Device Usage
- DoS: Uses only one device with DoS attack tools.
- DDoS: Uses multiple devices (often infected with malware) to launch the attack.
- Attack Types
- DoS: Includes attacks like Buffer Overflow, Ping of Death, Teardrop Attack, and Flooding Attack.
- DDoS: Includes Volumetric Attacks, Fragmentation Attacks, Application Layer Attacks, and Protocol Attacks.
Botnets in DDoS Attacks:
- Botnets: These are networks of compromised devices (infected with malware, called bots) used to launch DDoS attacks. The attacker can control a large number of bots, making it difficult for the victim to mitigate the attack. The botnet floods the victim’s server with excessive requests, overwhelming it and causing downtime.
Who is Responsible for DDoS Attacks?
- Motivations: The reasons behind DDoS attacks vary, including political agendas, revenge, business competition, criminal activities, or activism.
- Perpetrators: Potential attackers could include governments, terrorist groups, disgruntled employees, or independent hackers (hacktivists).
- Common Targets: High-profile organizations and sectors like financial institutions, technology companies (e.g., Microsoft), and media outlets (e.g., BBC).
- Notable Incidents:
- Dyn attack: In 2016, a DDoS attack targeted Dyn, a company managing web traffic for major websites like Twitter, Netflix, and Reddit, causing widespread outages.
- MI5 and BBC: Both entities have faced DDoS attacks as part of their vulnerabilities to such cyberattacks.
Kaveri 2.0’s Struggle with the DDoS Attack:
- Impact on Kaveri 2.0 Portal
- In December 2024 and January 2025, Kaveri 2.0 began experiencing severe performance issues.
- Fake accounts were created on the portal, and entries were made using these accounts, overwhelming the system.
- The attack involved 62 email accounts from 14 IP addresses, demonstrating the distributed nature of the assault.
- In January 2025, the portal saw a massive surge in traffic, particularly for Encumbrance Certificate (EC) searches, with 2 lakh requests in just two hours.
- This surge was eight times higher than usual, which ultimately crippled the portal, affecting property registrations.
- Attack Details
- Malicious users, employing random keywords, initiated high volumes of requests, leading to system overload.
- The Kaveri 2.0 portal was unable to handle the deluge of requests, severely disrupting services and reducing the number of registrations processed.
Mitigation Strategies Against DDoS Attacks:
- Preventive Measures for DDoS Attacks
- To guard against such attacks, organizations can implement various traffic filtering and security mechanisms:
- Advanced Traffic Filtering: Tools can help distinguish between legitimate and malicious traffic, preventing DDoS traffic from reaching the target.
- Monitoring Tools: Continuous monitoring helps in identifying unusual traffic patterns, enabling organizations to take pre-emptive actions.
- Rate Limiting: This mechanism controls the number of requests a user can make within a specific timeframe, preventing system overload.
- Bot Detection Technologies: Tools like CAPTCHA challenges and behavioral analysis can help identify and block automated bots used in DDoS attacks.
- Additional Security Measures
- Robust Authentication: Implementing strong authentication protocols helps prevent unauthorized access and strengthens overall security.
- Regular Security Audits: Periodic audits can help identify vulnerabilities and address them proactively.
- Collaboration with Cybersecurity Agencies: Organizations should collaborate with cybersecurity agencies to investigate attacks, share information, and develop mitigation strategies.
- Incident Response Team: A dedicated team should be in place to respond quickly to any security incidents and mitigate their impact.
- For the User
- Awareness about Social Engineering Attacks: Users should be aware of phishing attempts and other social engineering tactics that could compromise their accounts, further amplifying the effects of a DDoS attack.
- To guard against such attacks, organizations can implement various traffic filtering and security mechanisms:
Broader Implications:
- What’s Next for Kaveri 2.0?
- Following the DDoS attack, registrations on Kaveri 2.0 dropped significantly on February 1 and 4, 2025.
- The portal was restored by February 5, but the attack serves as a wake-up call for government agencies and organizations to prioritize cybersecurity.
- Cybersecurity measures should be integrated into the development and maintenance of digital infrastructure, especially for government services like Kaveri 2.0, which handle sensitive tasks like property registration.
- Broader Implications for Organizations
- The Kaveri 2.0 attack emphasizes the importance of cybersecurity in public sector infrastructure.
- Given the increasing reliance on digital services, organizations must invest in robust security frameworks to protect against DDoS and other cyberattacks.
- Other Major DDoS Attacks
- The X platform, owned by Elon Musk, was targeted in August 2024, leading to delays and disruptions on the platform.
- A previous attack in 2015 saw Microsoft-owned GitHub targeted by a China-based botnet, aiming at projects that circumvented Chinese censorship.
- These incidents highlight that even high-profile platforms and major organizations are vulnerable to cyber threats and must take proactive measures to mitigate such attacks.
- DDoS attacks overwhelm a system with high traffic, disrupting services and leading to downtime.
- The Kaveri 2.0 portal in Karnataka faced a crippling DDoS attack, resulting in the loss of property registrations.
- To mitigate DDoS attacks, organizations must implement strong filtering, traffic monitoring, rate limiting, and bot detection technologies.
- The attack on Kaveri 2.0 underscores the need for robust cybersecurity measures, especially for public sector digital services.
Conclusion:
The DDoS attack on Kaveri 2.0 highlights the increasing risks faced by digital platforms, particularly government portals. It underscores the urgent need for enhanced cybersecurity measures, proactive monitoring, and rapid response strategies to protect essential services from disruptions.
Source: IE
Mains Practice Question:
Discuss the significance of strengthening cybersecurity measures in government digital platforms. How can proactive steps prevent the impact of DDoS attacks and other cyber threats?